Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 17 junho 2024

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Load data using a third-party application, BigQuery
Technologies, Free Full-Text

Analysis of dynamic code updating in Android with security
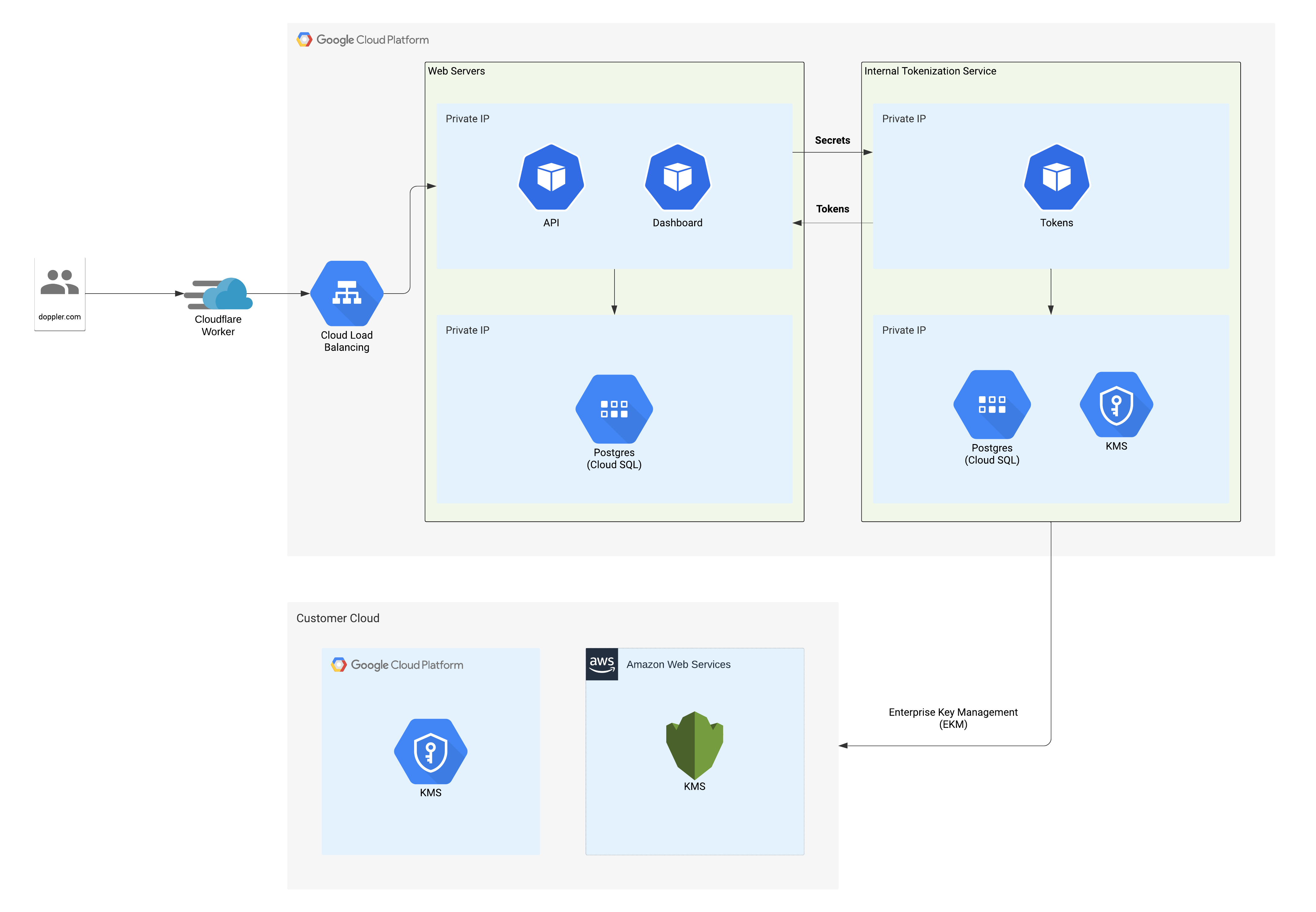
Secrets Manager

Android: With Android 14, Google has a new plan to make your

Android App Disguised as a QR scanner, Spreads Joker Variant Trojan

ROC curve for malware detection using feature hashing on

Google Play threat market: overview of dark web offers
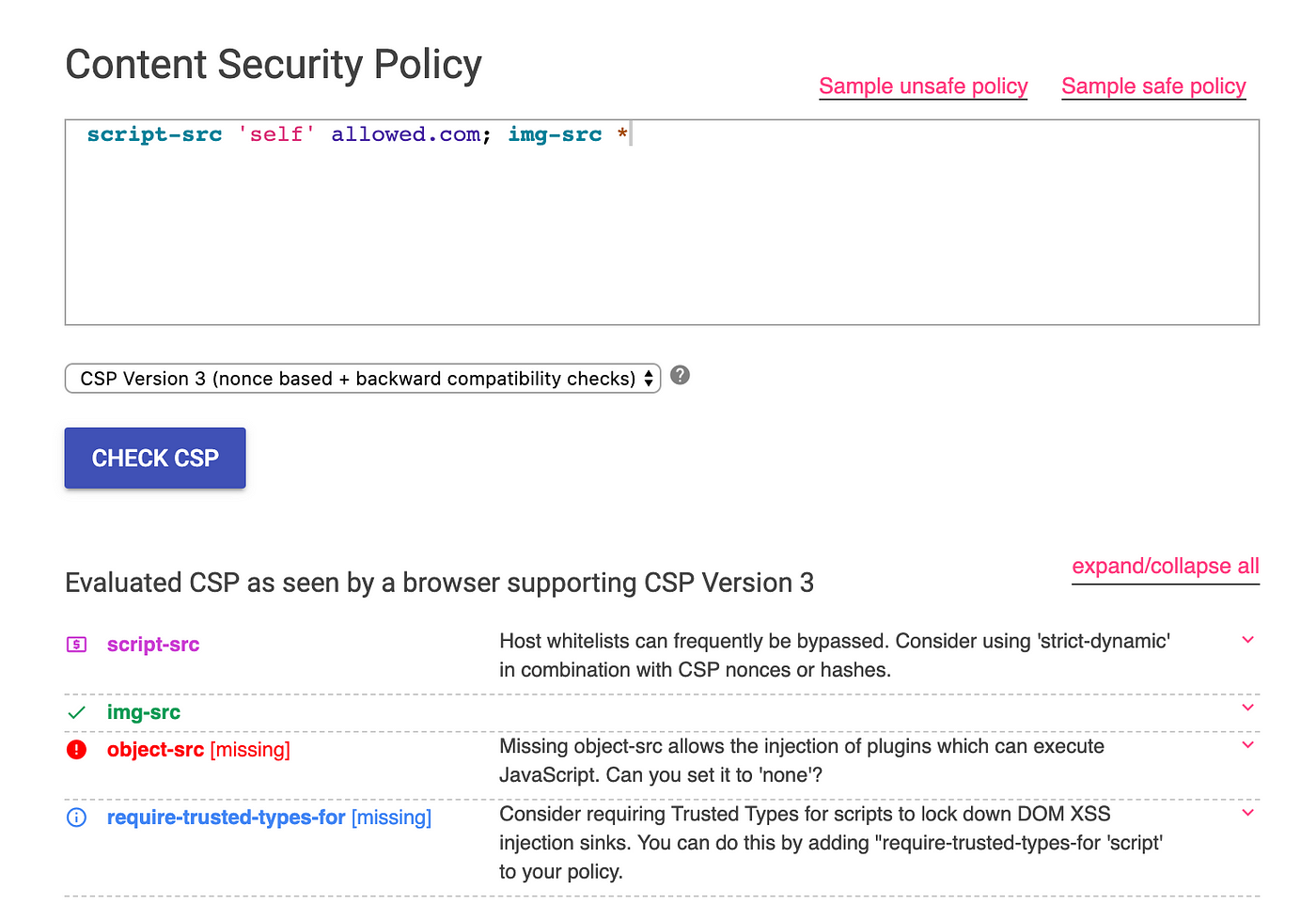
Content Security Bypass Techniques to perform XSS

Anti-Tampering - Zimperium Glossary
Attackers use dynamic code loading to bypass Google Play store's
Recomendado para você
-
 Roblox Evade – Free codes (December 2023) - Xfire17 junho 2024
Roblox Evade – Free codes (December 2023) - Xfire17 junho 2024 -
 All Evade Codes in Roblox (December 2023)17 junho 2024
All Evade Codes in Roblox (December 2023)17 junho 2024 -
 Roblox Evade Codes (June 2023): Free Customization17 junho 2024
Roblox Evade Codes (June 2023): Free Customization17 junho 2024 -
 trooper evade roblox17 junho 2024
trooper evade roblox17 junho 2024 -
 read desc) NEW EVADE SECRET CODES! (2023 Celebration unusual showcase) - Roblox Evade17 junho 2024
read desc) NEW EVADE SECRET CODES! (2023 Celebration unusual showcase) - Roblox Evade17 junho 2024 -
 NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES17 junho 2024
NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES17 junho 2024 -
 Pro-Palestinian social media users turn to algospeak to avoid17 junho 2024
Pro-Palestinian social media users turn to algospeak to avoid17 junho 2024 -
 NEW* ALL WORKING CODES FOR Evade IN OCTOBER 2023! ROBLOX Evade17 junho 2024
NEW* ALL WORKING CODES FOR Evade IN OCTOBER 2023! ROBLOX Evade17 junho 2024 -
 All Secret Evade Codes 2023 - Roblox Code17 junho 2024
All Secret Evade Codes 2023 - Roblox Code17 junho 2024 -
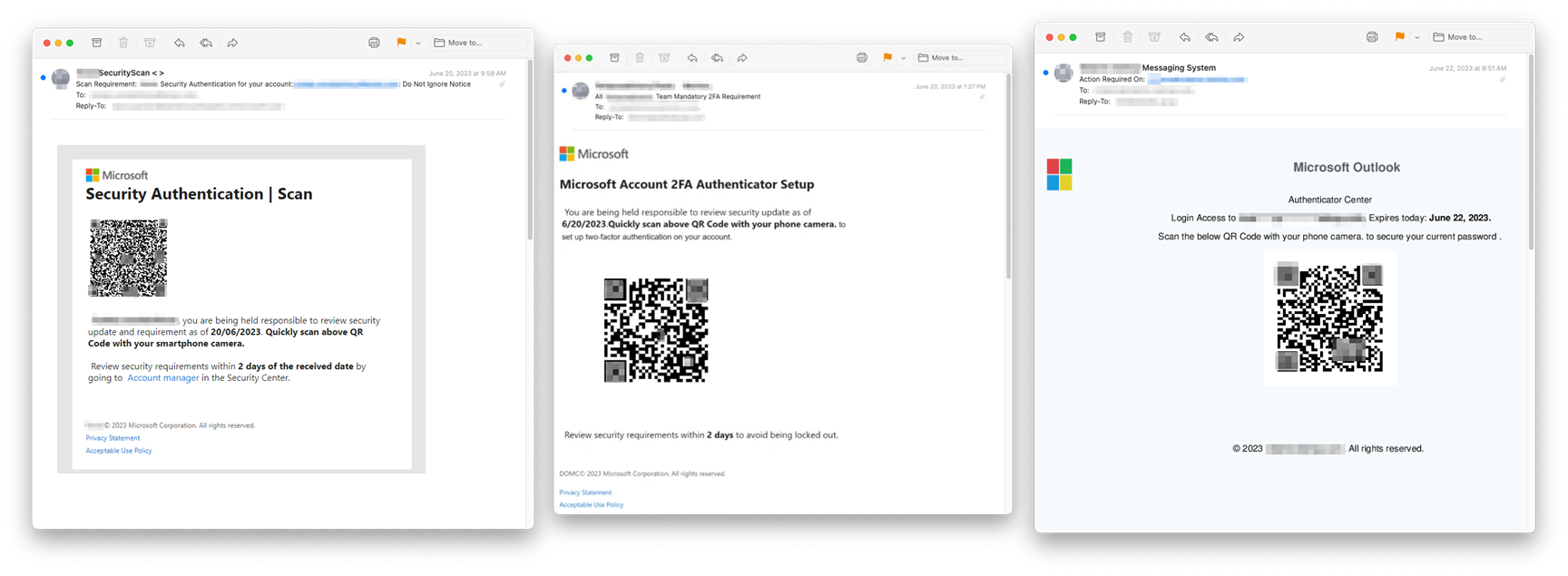 Cybercriminals are circumventing email security with image-based17 junho 2024
Cybercriminals are circumventing email security with image-based17 junho 2024
você pode gostar
-
 Vila Nova x Juventude- Palpite, escalações, estatísticas - 30/04/202317 junho 2024
Vila Nova x Juventude- Palpite, escalações, estatísticas - 30/04/202317 junho 2024 -
 JK Gumi (Mito/Kaede/Rin) vs Lolico-roll (Kokoro/Luis/Lain) 3D collab! : r/Nijisanji17 junho 2024
JK Gumi (Mito/Kaede/Rin) vs Lolico-roll (Kokoro/Luis/Lain) 3D collab! : r/Nijisanji17 junho 2024 -
Phoenix Fruit - Blox Fruits17 junho 2024
-
 Teclado gamer Knup KP-TM010 QWERTY Outemu DIY Blue português17 junho 2024
Teclado gamer Knup KP-TM010 QWERTY Outemu DIY Blue português17 junho 2024 -
 Copa do Mundo: o que esperar do jogo do Brasil x Croácia amanhã17 junho 2024
Copa do Mundo: o que esperar do jogo do Brasil x Croácia amanhã17 junho 2024 -
 The Ping-Pong Club (Manga) - TV Tropes17 junho 2024
The Ping-Pong Club (Manga) - TV Tropes17 junho 2024 -
 Berserk (1997) Rewatch - Episode 2 : r/anime17 junho 2024
Berserk (1997) Rewatch - Episode 2 : r/anime17 junho 2024 -
Todos os jogos do Palmeiras no Brasileirão #palmeiras #verdao #sep17 junho 2024
-
Recordamos o Porsche 911 Dakar, o clássico Ford Mustang e o Cupra Urban Rebel - SIC Notícias17 junho 2024
-
 Berserk (2016) Episódio 03 Online - Animes Online17 junho 2024
Berserk (2016) Episódio 03 Online - Animes Online17 junho 2024