Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Last updated 01 junho 2024

[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]

New Microsoft Incident Response team guide shares best practices

Is The CIA Triad Relevant? Confidentiality, Integrity

Security Operations (SecOps) - Enterprise Security - ServiceNow

Information & Cyber Security Policy Templates
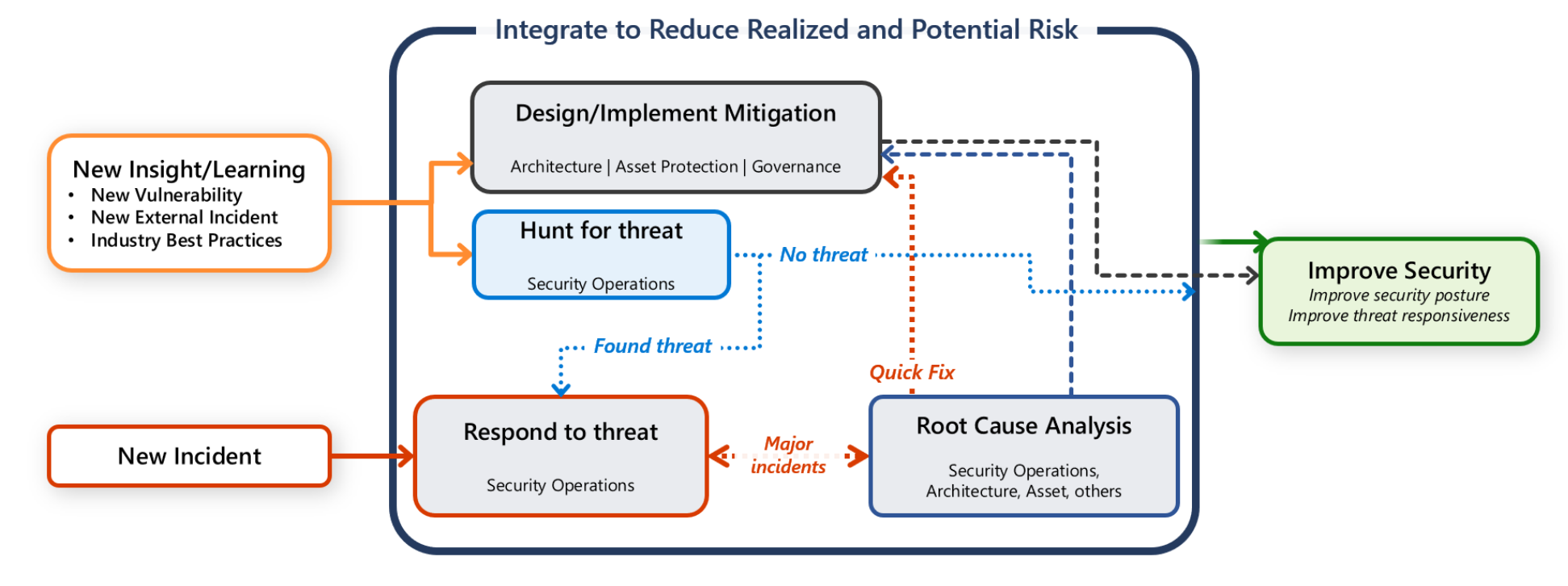
Recommendations for security incident response - Microsoft Azure
Incident Response SANS: The 6 Steps in Depth
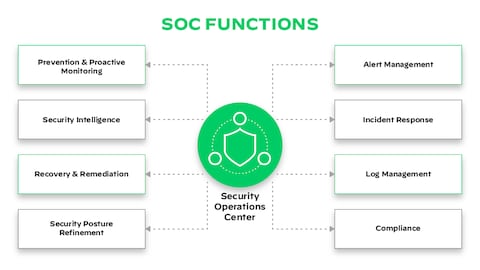
What Is a Security Operations Center (SOC)? - Palo Alto Networks

6+ Cybersecurity Resume Examples [with Guidance]

The complete information security incident management process

Information Security, Global
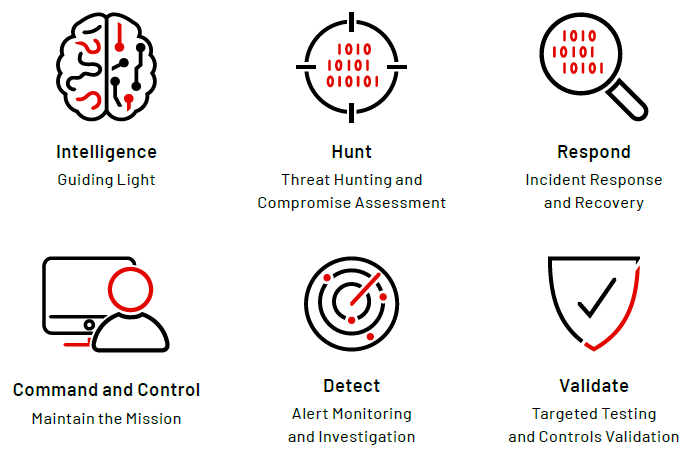
Improve Your Cyber Defenses with these 6 Critical Functions
Recomendado para você
-
 Incident Response Phases - Lessons Learned - Halkyn Security Blog01 junho 2024
Incident Response Phases - Lessons Learned - Halkyn Security Blog01 junho 2024 -
 Lessons learned, feedback and continuously improving your Health01 junho 2024
Lessons learned, feedback and continuously improving your Health01 junho 2024 -
 The Daily Life — #learning is a #gift when #pain is your #teacher..01 junho 2024
The Daily Life — #learning is a #gift when #pain is your #teacher..01 junho 2024 -
 Process Safety Incidents: Causes, Consequences, and Lessons Learned01 junho 2024
Process Safety Incidents: Causes, Consequences, and Lessons Learned01 junho 2024 -
 Keyword:incident analysis - FasterCapital01 junho 2024
Keyword:incident analysis - FasterCapital01 junho 2024 -
 PDF) Lessons learnt from the development of the Patient Safety01 junho 2024
PDF) Lessons learnt from the development of the Patient Safety01 junho 2024 -
 AWS Incident Detection and Response: Rapid Security Incident Response01 junho 2024
AWS Incident Detection and Response: Rapid Security Incident Response01 junho 2024 -
 Learning from cyber security incidents: A systematic review and01 junho 2024
Learning from cyber security incidents: A systematic review and01 junho 2024 -
EUROPA - MINERVA Home Page - European Commission - Publications01 junho 2024
-
 PPT - Responding to Safety & Environmental Incidents01 junho 2024
PPT - Responding to Safety & Environmental Incidents01 junho 2024
você pode gostar
-
 BEBÊ REBORN REALISTA MENINA TATA LAÇO AZUL01 junho 2024
BEBÊ REBORN REALISTA MENINA TATA LAÇO AZUL01 junho 2024 -
 Tatoo photo Joey Attard - (1052750)01 junho 2024
Tatoo photo Joey Attard - (1052750)01 junho 2024 -
 Resident Evil 4 Remake will have Ray Tracing, PC requirements revealed01 junho 2024
Resident Evil 4 Remake will have Ray Tracing, PC requirements revealed01 junho 2024 -
 Spy x Family: 7 motivos para assistir o anime do momento01 junho 2024
Spy x Family: 7 motivos para assistir o anime do momento01 junho 2024 -
 O Mistério de Hataraku Maou-sama: O Anime de sucesso sem 2ª01 junho 2024
O Mistério de Hataraku Maou-sama: O Anime de sucesso sem 2ª01 junho 2024 -
 Proto:Sonic the Hedgehog 2 (Genesis)/CENSOR Prototype - The Cutting Room Floor01 junho 2024
Proto:Sonic the Hedgehog 2 (Genesis)/CENSOR Prototype - The Cutting Room Floor01 junho 2024 -
 Caneca de café Team GB Grã-Bretanha Jogos Paralímpicos do Reino Unido01 junho 2024
Caneca de café Team GB Grã-Bretanha Jogos Paralímpicos do Reino Unido01 junho 2024 -
 Bubble Witch 3 Saga::Appstore for Android01 junho 2024
Bubble Witch 3 Saga::Appstore for Android01 junho 2024 -
 Bem-humorado, Djokovic se derrete em elogios a Guga - ESPN01 junho 2024
Bem-humorado, Djokovic se derrete em elogios a Guga - ESPN01 junho 2024 -
howdy guys! here are my shrek-themed crocs! 🐊💚🤎 i used the01 junho 2024
